QoS - 2009-7-8 13:40:00
关于:hxxp://www.rzgl.gov.cn/img/storm.htm解密的日志(全体输出 - 2):
Level 0>http://www.rzgl.gov.cn/img/storm.htm
Level 1>http://www.rz168.com/edit/x.exe ●
日志由 Redoce1.9第68次修正版于 2009-7-8 下午 01:39:08 生成。
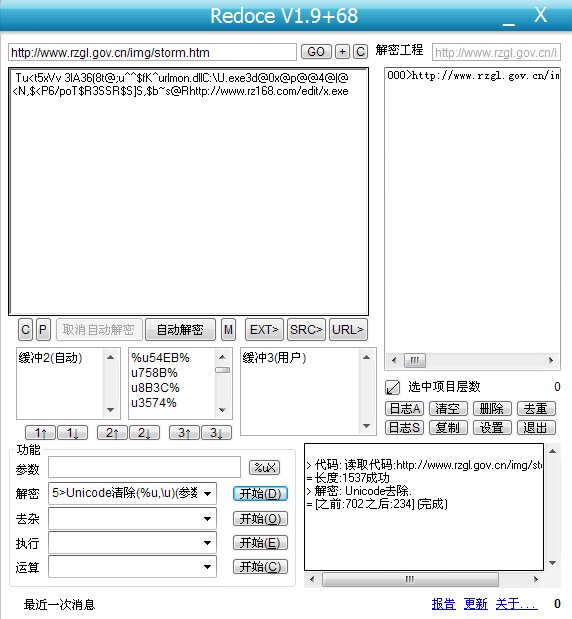
就解出一个:kaka3:
Level 0>http://www.rzgl.gov.cn/img/storm.htm
Level 1>http://www.rz168.com/edit/x.exe ●
日志由 Redoce1.9第68次修正版于 2009-7-8 下午 01:39:08 生成。
就解出一个:kaka3: